Identity & Access Management (IAM)
Zero Trust. Full Control. Seamless Access.
Cybersecurity / Identity and Access Management
Overview
Securing the right access for the right people at the right time.
Infinite’s IAM services help organizations streamline user access across applications, data, and systems while minimizing risk. Our approach is grounded in Zero Trust principles and built on modern frameworks like ICAM and RBAC/ABAC. Whether you’re managing cloud identities, enabling MFA, or automating provisioning, Infinite ensures secure and seamless access without compromising productivity.
Closed-Loop User Identity & Access Management Framework
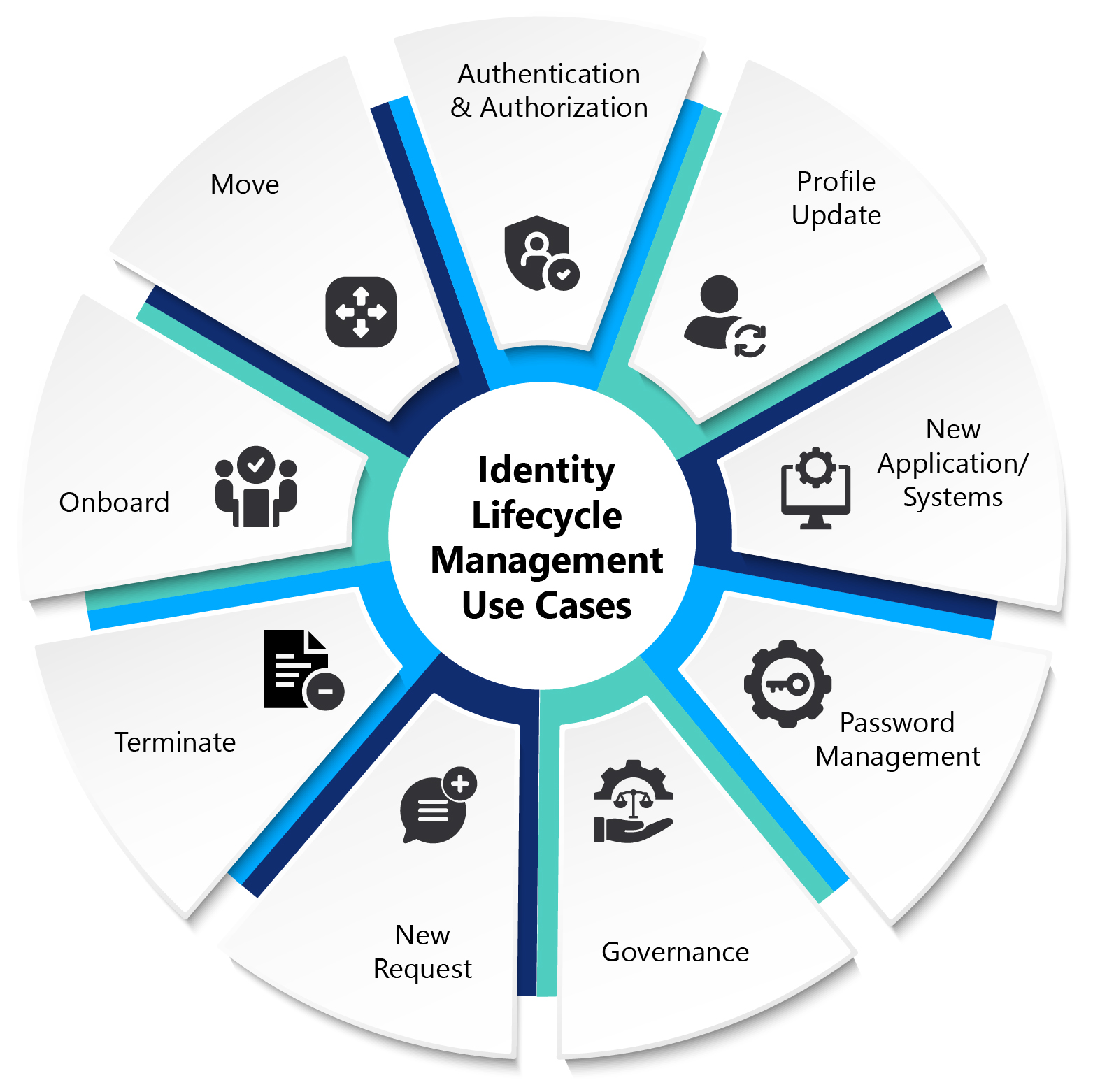
Authentication & Authorization
- Validate user identities
- Enable SSO services
- Determine the right access to systems
Profile Update
- Self-service
- Update personal information
- User attribute sync with other systems
New Application/ Systems
- Alignment with new apps
- New roles and access entitlements
Password Management
- Initial password
- Password reset
- Forgot password
- Password enquiry
Terminate
- Off-board Role/ Entitlement
Governance
- Implement NS IAM policies
- Support in defining IAM policies
- Conduct recertifications
- Audit logging and monitoring
- Reporting
New Request
- Access entitlement
- Approval processes
- Privilege / Admin rights
Onboard
- Initial New Role/Entitlement onboarding
- Grant privilege access (as needed)
- Birthright provisioning
- Enable MFA
- Segregation of duties
Move
- Roles and entitlements updates
- Lateral movement access
Pre-Onboarding
- Initiate contractual obligation/ documents
- User verification and background checks
- Attend mandatory trainings and KT
- Review, authorize, and provision access to the intended systems/applications
Post-Termination
- Completion of contractual obligations
- Cancellations or suspension of contracts
- Termination of third-party associates
- Confirm access revocation and reporting
Challenges & Solutions
Centralized identity governance with role- and attribute-based access control.
Unified MFA, SSO, and federation protocols across all apps and environments.
Lifecycle automation with policy-based provisioning and entitlement recertification.
Privileged Access Management (PAM), session control, and least-privilege enforcement.
Identity analytics, logging, and reporting integrated with regulatory frameworks.